Managing permissions for POD and SecureLink Jobs
In order to run POD or SecureLink Unveiler jobs, an API user needs to be setup with mutual TLS authentication and be granted the relevant permissions to perform one or more of the operations that are provided for running POD and SecureLink. This includes:
Masking
Unmasking
Remasking
Unveiling
These permissions are managed on a per-Team basis. For example, if an API user is granted a role enabling them to run Masking POD jobs in a team (Team A), that user will be allowed to run any masking POD job in that team. (This also applies to Unmasking and Unveiling).
This means that in order to run any POD Masking Job which belongs to Team A, the API user needs to have been assigned a role in Team A containing the Run POD permission for Masking Jobs.
See the permissions highlighted in the Create New Role dialog box:
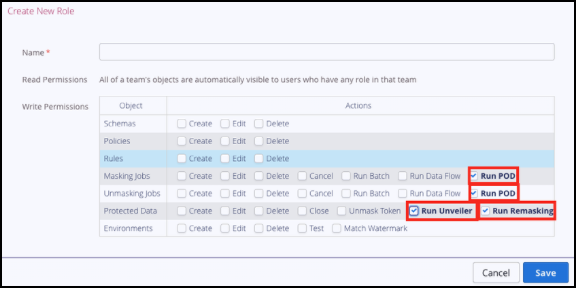
To run Remasking POD jobs within a single team, the following permissions need to have been assigned:
Run Remasking permission for Protected Data
Run POD permission for Masking Jobs
To run Remasking POD jobs between two teams (Team A and Team B) the following permissions need to have been assigned:
Run Remasking permission for Protected Data, for the team that owns the source POD Job (Team A).
Run POD permission for Masking Jobs for the team that owns the destination POD Job (Team B).
For more information about Permissions for users of Privitar, see Role Permissions.
