Architecture
This section describes the architecture of the Privitar AWS deployment together with information about the security implications of deploying AWS in your AWS Cloud environment.
Deployment architecture
The following diagram shows the overall architecture of the Privitar AWS Deployment and the associated AWS services that it uses:
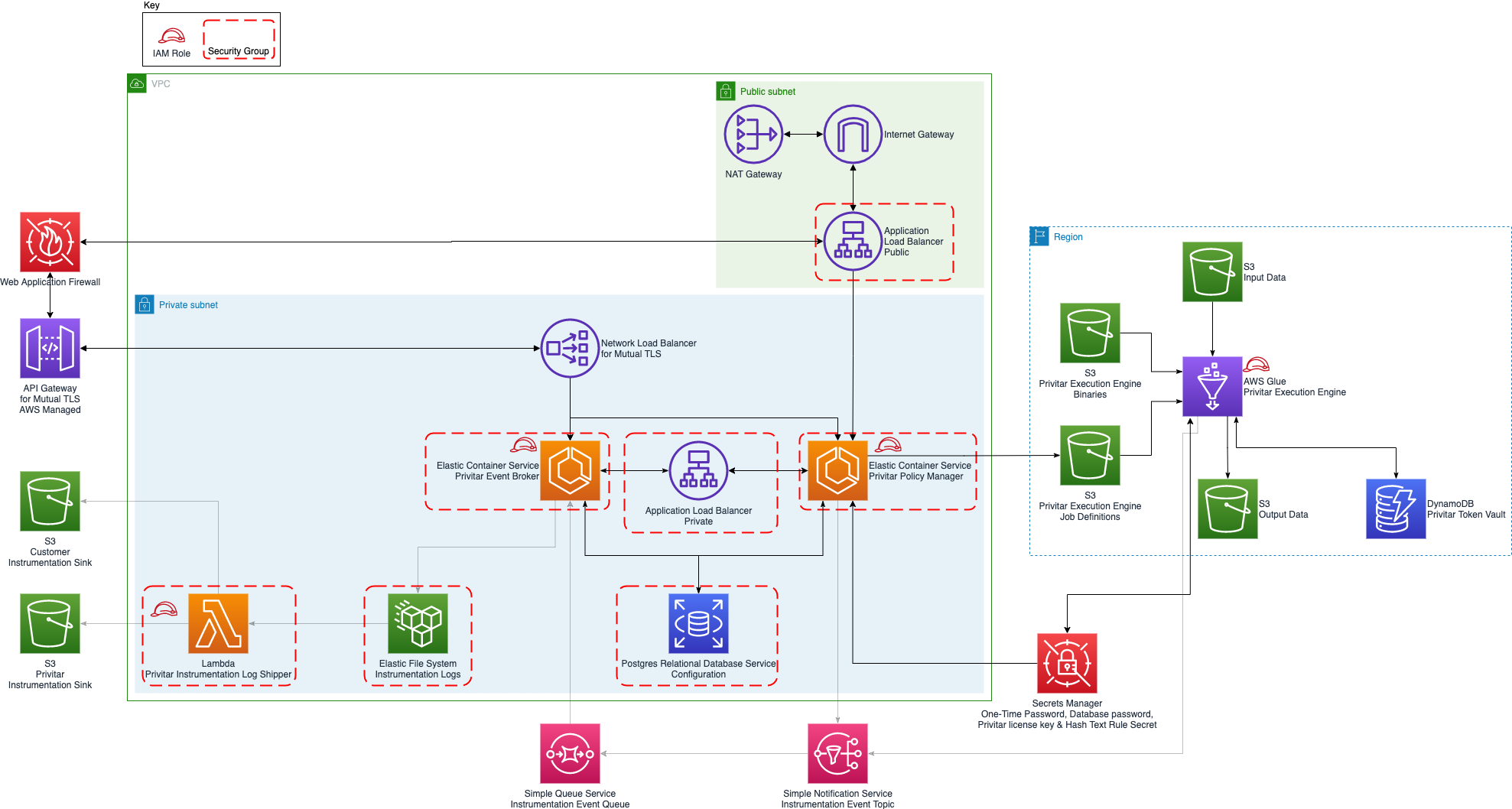 |
The following table describes the AWS services that are used in the deployment:
Service | Description |
|---|---|
Application Load Balancer and Network Load Balancer | Route traffic from the Internet to services, and between services. |
Web Application Firewall | Blocks known malicious entities and provides rate limiting. |
API Gateway | Terminate mutual TLS. |
Elastic Container Service with Fargate | Host the applications that comprise Privitar AWS. |
Relational Database Service | Store configuration and state for the applications that comprise Privitar AWS. |
Secrets Manager | Store sensitive infrastructure information. For example, the configuration database (ConfigDB) password, the SAML secret, JSON web token (JWT) secret, Privitar NOVLT secret, watermarking secrets, and any others. |
Simple Queue Service and Simple Notification Service | Route instrumentation telemetry data from Privitar Policy Manager and Glue execution environments to the Privitar Event Broker. |
Elastic File System | Store event broker instrumentation logs, prior to shipping. |
Lambda | Ship instrumentation logs and performs other small tasks. For example, key rolling. |
Glue | Infer from Glue Schema. Execute Privitar jobs in Glue ETL. |
DynamoDB | Store Privitar consistent tokenization mappings. This is referred to as the Token Vault. |
S3 | Store state, Glue ETL binaries, data, and logs. |
VPC networking | Core infrastructure for the network layer, including NAT gateway, internet gateway, VPC, subnets, security groups. |
Key Management System (KMS) | Encryption keys for resources created as part of this deployment. |
Deployment Security
There are certain security implications that you need to be aware of when deploying Privitar AWS.
Internet-facing components
The deployment contains internet facing components. This means that:
A Route53 registered domain and public hosted zone is required. This means that the domain name and certificates are public.
The AWS Application Load Balancer that the Route53 DNS A record points to is internet-facing.
The optional mutual TLS enabled AWS API Gateway is internet-facing.
AWS Glue
Glue jobs created by Privitar AWS currently run inside the AWS managed networks, and not inside customer owned VPCs. It should be noted that AWS managed networks have outbound internet access.